How does the Hacker?
Understood a business connected network are protected but a domestic connected network are not.
Trojan horse:
The trojan horse, get access to your remote computer.
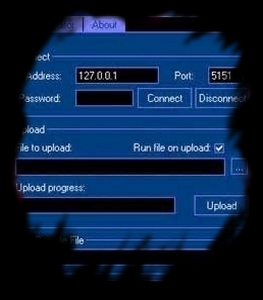
Keylogger:
The keylogger is a tool of a hacker. He catch to distant or directly to local machine all is push on the keyboard. Run to distant or to local by a man who had running the spyware by a floppy disk or cd-rom... on a sytem can be desaster for the victim.
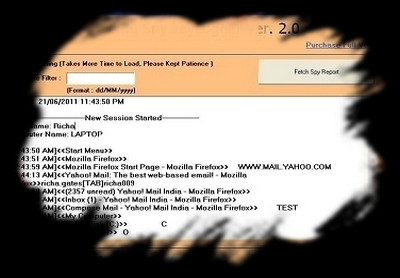
The email can be use by a hacker who can get your password for get access to your account mail as MSN or Gmail for example. The hacker try to get your confidence.
DDoS:
The hacker use a software of DDoS or Denial Of Service, the most popular or the most perfect for denied a site with or without anonym person who participate to attack.
We can talk about a rootkit who are a malware used by the hacker for do a DDoS, exploit or spam...